(CCDCOE / June 2010)
My original brief was to talk on how i would go about attacking a modern connected state. I noticed that Charlie (Miller) was covering this topic, so opted to go another route.
For this talk my point is simply to point out, that there are probably some big holes in your current threat model.
I’m from South Africa, and although WGN News sees very little difference between South America and South Africa, they are different places.
The only really important point on this slide is that i’ve been doing this for a while.
(this is a slide that should follow most Bio slides.. and if it cant be answered, it probably means that the previous slide should be skipped) :>
I’m not running a Pen-Test company anymore, and i’m not a defense contractor so i don’t really have a vested interest in either over or under hyping this topic.
I do have a fair bit of experience breaking stuff, breaking into stuff and building and managing teams to do just that.
I’m not going to cover the usual cyber-war red-herrings.
I won’t try to convince you that it is or isn’t real and i certainly won’t make any of the “CyberWar is Bullsh*t” type of sweeping statements that make opinionated sec-pundits famous.
I’m just going to raise 5 questions, and you should be checking them against your threat model to see if you currently cater for it.
(Sadly, i don’t necessarily have answers to all of them.. but if you are at least more aware of the questions, you will be better off)
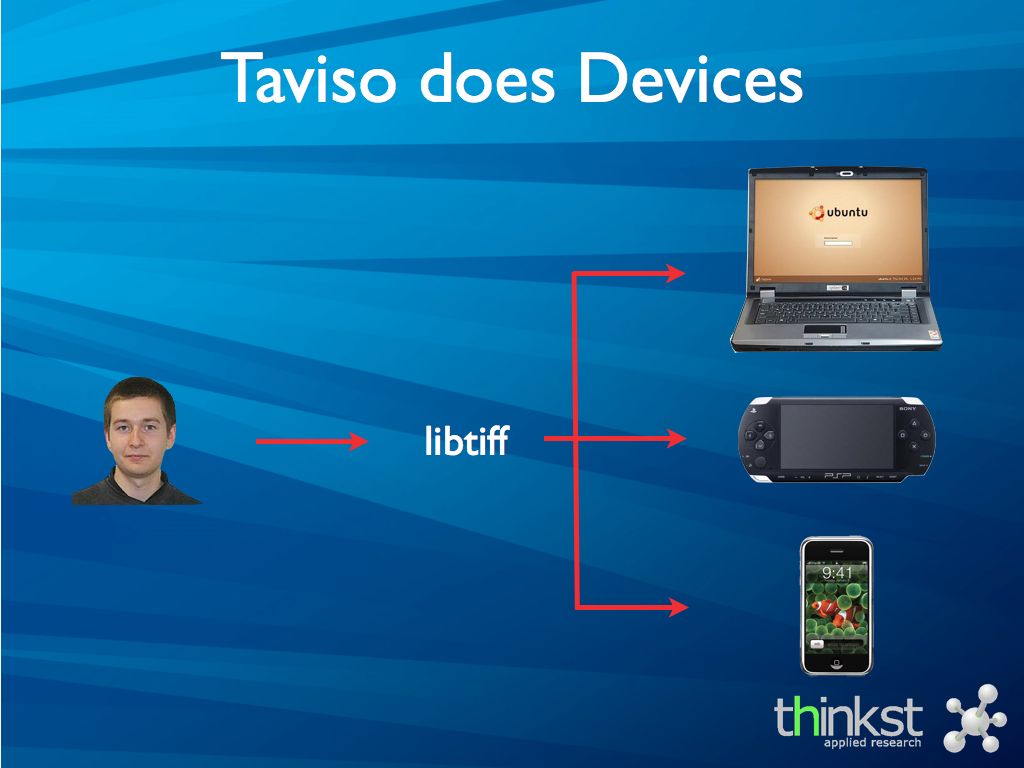
The first question is if your threat model covers “Tavis Ormanday”. A quick show of hands shows that 1 person in the audience has heard of Tavis.
A few years ago, Taviso published details on bugs found in libtiff. The exploitable bugs broke just about every *nix known to man.
This means that for a while, all of you were vulnerable to Tavis (and the friends he shared details with) and there was little you could do about it.
Interestingly enough, libtiff was used in both the PSP and iPhone which meant that the same bug was leaned on heavily in early jailbreaks of those devices. So.. Tavis owned all your *nix boxes and consumer devices too.
This year, he played a little with Windows, and did what he does best..
Quick point and click demonstration of tavis’ vdmallowed.c exploit.
Although the bug isnt exactly riveting spectator viewing, it does have an interesting element to it..
And that is the duration the bug has been alive. The bug in the VM Emulation code has existed since NT3.51, meaning its been carried around for about 17 years.
This is one hell of a window of exposure.
Consider then that Tavis alone has been able to own you Linux/Unix/Windows systems quite trivially.
Consider also that even if you heard of Tavis, you probably never heard of Niacin or Dre. (These 2 guys were pretty unknown to us, till they performed the cool hacks needed for jailbreaking)
The key thing here, is that while Tavis is clearly a very bright guy, he isn’t the only person capable of such exploits.
For his CanSec talk, Charlie (who speaks tomorrow) aimed a fuzzer at Apple and generated 20 useful bugs.
Yesterday he demo’d a bug to the journalists that is classic 0day.
Not reported to Apple yet, so unlikely to be fixed anytime soon.
You browse to his link, and he owns your computer.
So are you currently able to defend against them?
The 2nd question, is more simple, and speaks directly to the asymmetry problem. We have been training companies/individuals on how to break into networks for many years, and we have always espoused the importance of solid footprinting. Discovering the one box connected to a supplier thats allowed a backdoor into the network makes sense, so its always been important to us to fully understand the targets network footprint. So we obviously built tools and scripts to help automate this. In 2003, we wrapped these scripts up in a GUI, and gave it a pretty interface. So you click “South Africa” and it foot prints key industries, businesses, ISPs etc. It then footprints them, giving you DNS entries, network blocks, etc.
And again it makes it obvious what a huge asymmetry problem we have. The defenders need to defend everywhere and be good everywhere, while the attackers can get lucky or win just in on area.
Now that tool was a little bit of eye-candy, because if you are honest, you don’t need this to be footprinted in 10 minutes while you on stage. This stuff can be done slowly over months, so its barely detectable at all. But it does point to an interesting point.
If i wanted to attack your country, i would be an idiot to aim first at your .mil fortified networks. Instead i’ll aim at your newspapers to spread some Fear, and i’ll aim at your banks to do serious de-stabiliztion, or at your ISP’s or Cell Phone providers.. There’s gold in them thar hills, and you probably not in a position to protect yourself with so many possible targets for me.

A key thing that you need to remember is that professionals are more than just a 0day.
What professionals are doing all the time is building and improving on their tool chains.
Almost every public attack we see is quoted by some reporter as “sophisticated” which makes real professionals really wince.
You can spot sophistication in toolchains, and we have yet to see really sophisticated attacks.
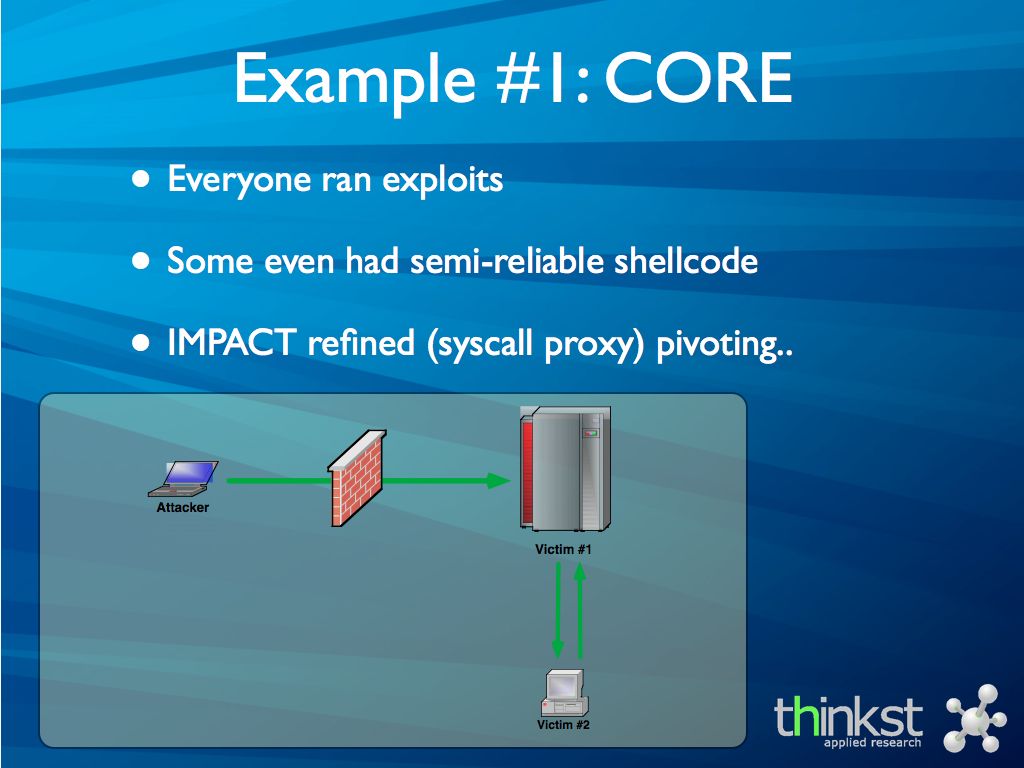
In the early 2000’s pen-testing was pretty ad-hoc and running exploits were pretty close to pot-luck.
Once you compromised your first host, you would then spend time building your toolchain on that host, attacking internals boxes and funneling your harvested data out.
The guys from CORE built syscall proxying into their Impact tool, and added “pivoting” into our lexicon allowing an operator to pivot his attack reliably, comfortably and repeatably from his attack machine.
They built their toolchain around it..
Since this is the tech-track, im supposed to show you a little eye candy, so i’ve chosen to walk you through some (hopefully while making my point).
At some point we came up against a web-app that was vulnerable to a code injection attack. We could get the server to execute our commands but could never get feedback from the server. So in the end we used timing as a data channel. [The demonstration shows code injection, where the results of the command are parsed and broken into a bit-stream. We then have the application “sleep(n)” for every bit thats a 1 and sleep(0) for every bit thats a 0. By timing the page response, we extract data from the server.]
As an exploit against that single server, it was already pretty cute, but because we do this for a living, our next step was to generalize the solution.
So when we bumped into SQL injection attacks where the injected machine had no route out of the network, we had timing built in as a channel.
Our tool, “squeeza” then had timing as a vector out.
in 2008, we demonstrated a tool for tunneling data into networks over HTTP or HTTPS
[demo: 3]
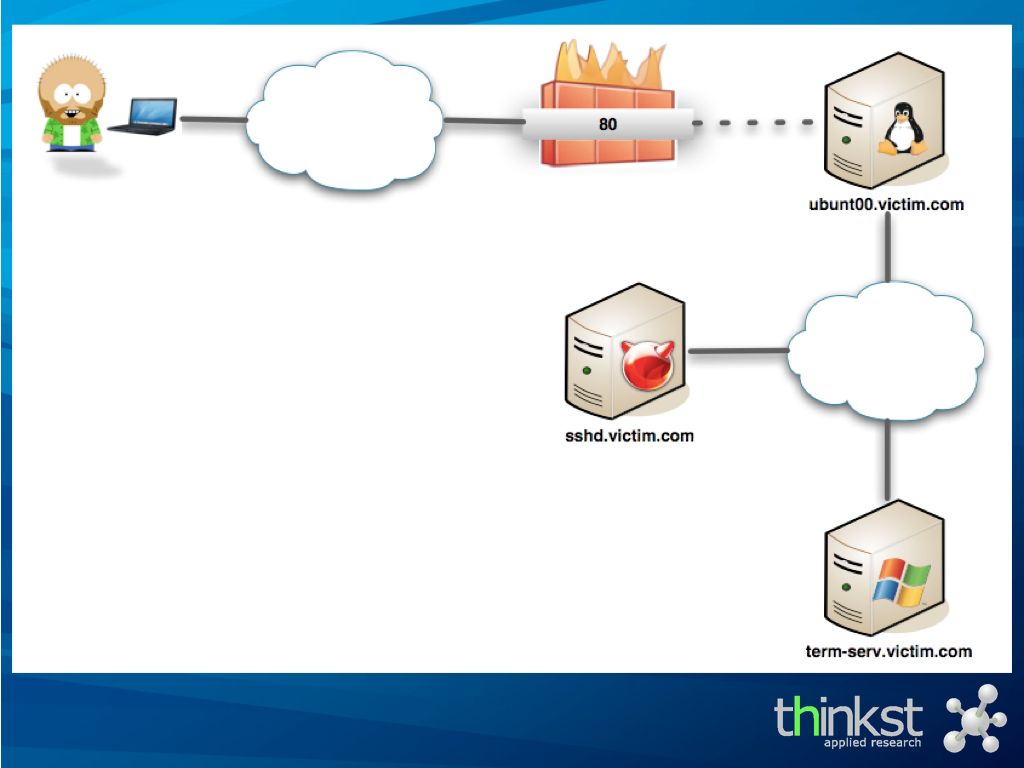
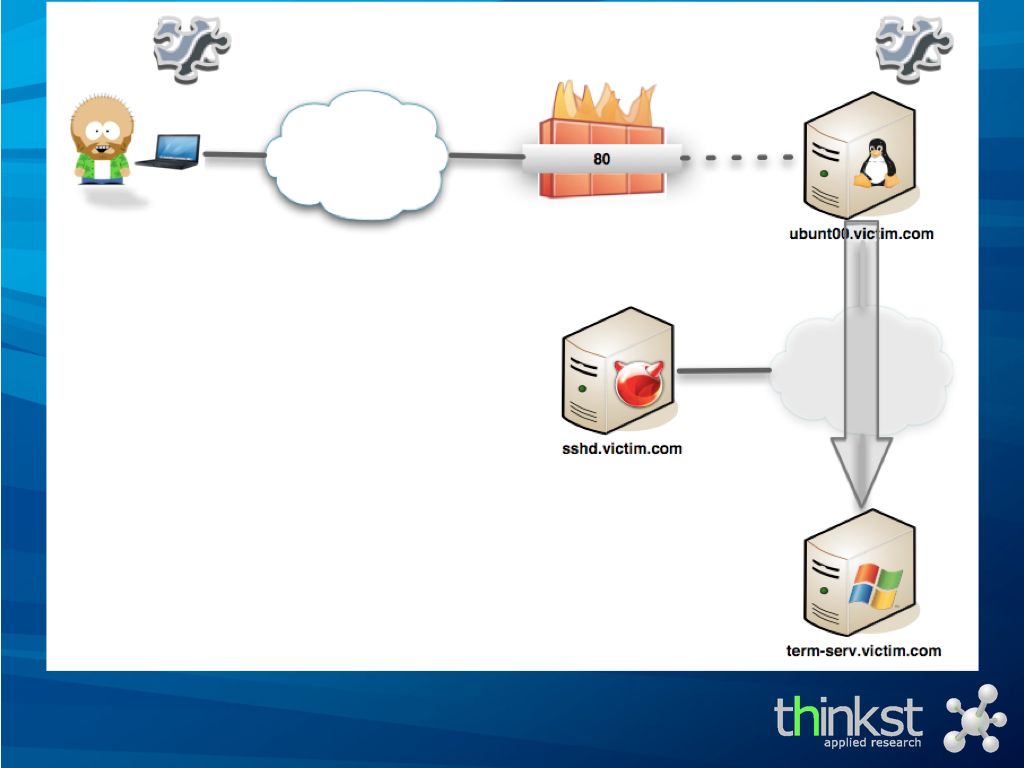
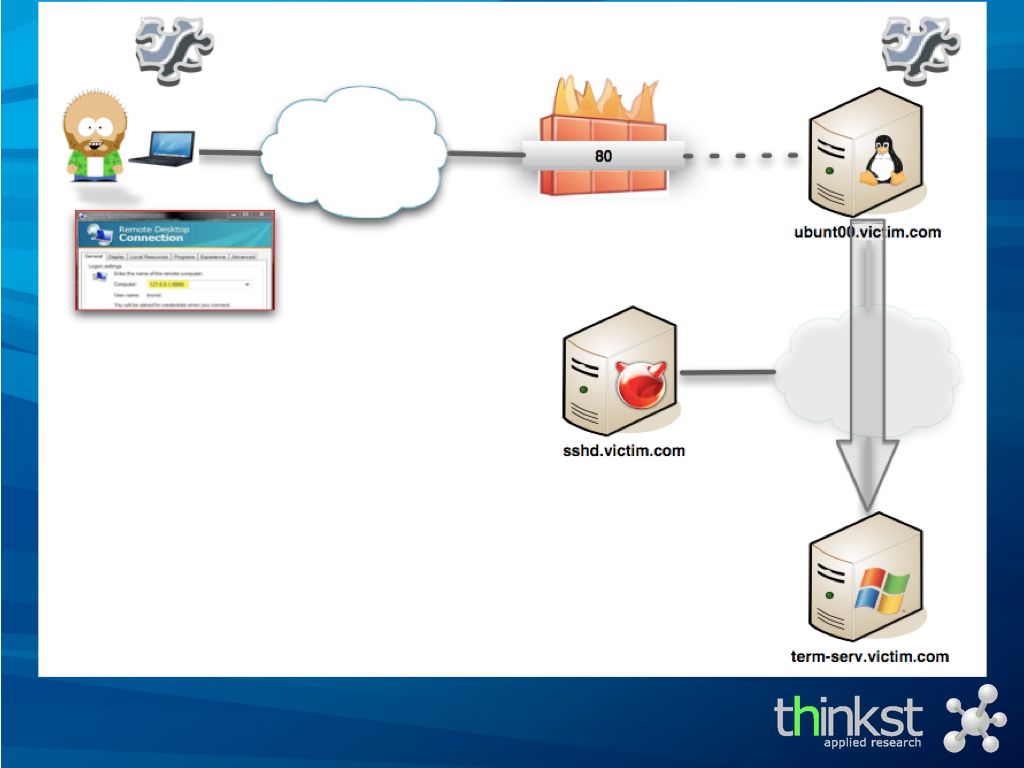
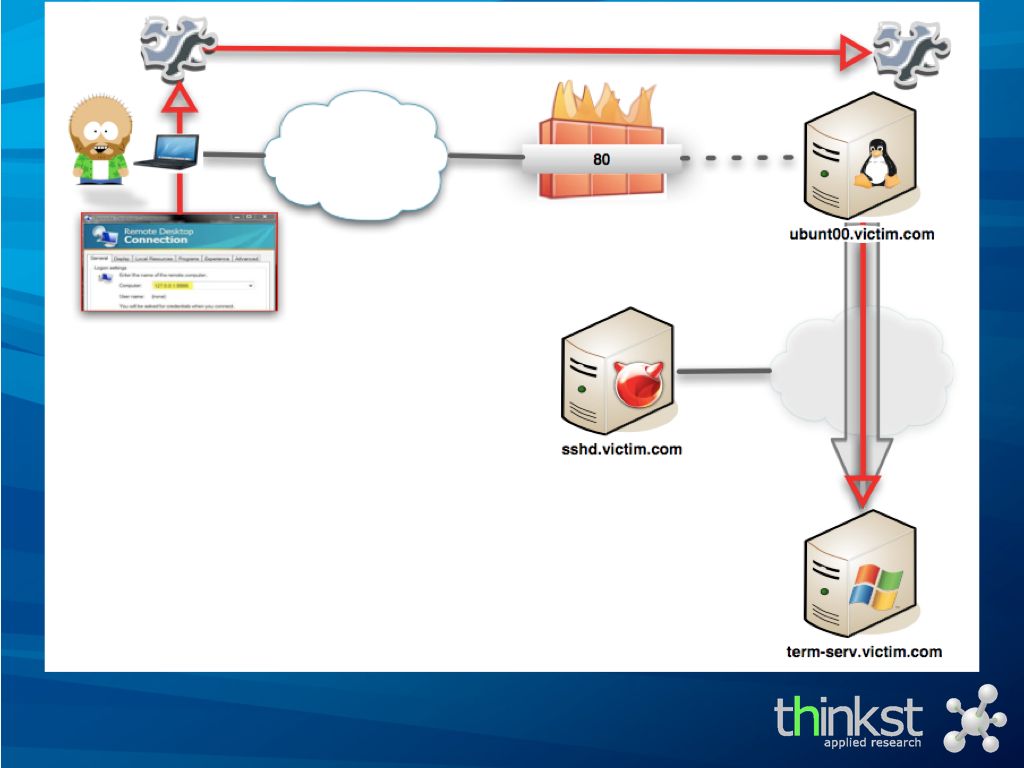
the scenario is that having already compromised the initial webserver, we now want to make connections to the internal Terminal Server.
By uploading a piece of code to the compromised webserver, and running a custom local proxy on our machine, we are all set.
We aim our RDP client at our local proxy, which translates the TCP to valid HTTP (or HTTPS) requests to the compromised webserver..
.. where our server component translates this back to TCP to the internal terminal server box.
Now this was cool, and helped us through many sticky networks…
..but then we also published techniques that allow you to build a binary inside SQL server through SQL Injection.
So the obvious step was another toolchain jump.
So we demo’d building a binary that is capable of doing the same timing abstraction, so that we can aim our RDP client at our proxy, that talks to squeeza, that talks sql injection in one direction (reads timing differences in the other direction) to our created binary inside SQL Server which talks TCP to the internal Terminal Server.
Now the point is not that we have too much time on our hands, but just that our toolchain just keeps growing.. because thats what (professional) attackers do..
For my 2nd last question, im going to raise some ugly points.
I intuitively had some guesses to these, but since i didn’t want to just say “trust me”, i sent some questions to people in the industry who have been doing this for a while.
(I made sure not to give my answers first to avoid anchoring the answers too much, but here are some of them, with the responses.)
The first question was simply to ask “For a few hundred thousand, could you put together a team that would break in just about anywhere?”
im from .za – Yes,
Saumil used to head up Foundstones India operations – Yes,
Ivan heads Core Security based in Boston and Argentina – Yes,
FX who heads recuritylabs in Germany – Yes.
Question 2 was to determine likelihood of success. I.e. if these guys say they can put together their team for a few hundred k, how do they rate their chances?
I can tell you that this answer includes some humilty padding. I.e. to avoid sounding overconfident / assy, most people round this down, but still come in at between 90% and 100%.
This means we are saying that in a fixed time period project, with a few choice resources, given a target, 90%-100% of the time, we win!
And the last ugly question is simple:
If you say “my team would break in if they cost me XX”, what is XX ? in USD
The sweet spot appears to be that for just under half a million dollars, you would have joy.
Ivan and FX both caveated their answers but the general number still seems sane.
That Question alone should be really scary, because 500k is less than what some companies will pay for their anti-virus bills.
The 5th point i think your threat model probably mis-handles is where you expect the threats to come from.
If i were to ponder capability, off the top of my head we have seen awesome stuff from LSD and Invisible things based in Poland.
Dave Aitels immunity team is based in USA with talent all over.
Core lives in Argentina with Saumil in India and SK Chong in Malaysia.
This list isn’t meant to be exhaustive by any stretch. It’s simply to show you that the the NATO countries dont have a monopoly on talent.
So.. in quick summary, you need to realize that the cost of attacking is much much cheaper than defense.
You need to know that none of the attacks we have yet seen qualify as “complex attacks”.
You need to keep in mind that we will aim at more than just your .mil boxes which makes the problem quite difficult to get a handle on.
I guess the bottom line here is that a reasonably funded intelligent adversary can make inroads doing what some of us have been doing for a while..
In general, the attacks we are seeing are the sort of buckshot, spray and pray attacks that professionals won’t use (unless they are using them as cover).
If you see obvious signs and defacements.. it’s safe to assume you are playing with kids, not pros.
Keep in mind that professionals don’t get spotted with 10 seconds of tcpdump / analysis..
Please feel free to add comments, on the blog, or mail thoughts / feedback to
haroon@thinkst.com(or go completely new-school and message
@haroonmeer on twitter)