Last month Florian Roth (cyb3rops) reacted to the news of Mimikatz dumping RDP credentials by asking how we could easily inject fake credentials into machines.
 |
| https://twitter.com/cyb3rops/status/1397440903476883458 |
Markus Neis pointed out that on Windows, cmdkey allows you to do this:
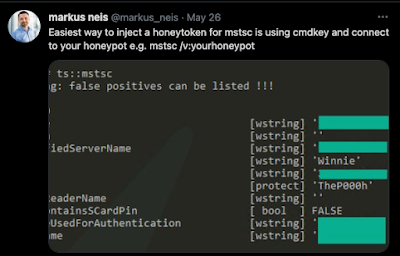 |
| https://twitter.com/markus_neis/status/1397472760859856897 |
This is pretty awesome. Mimikatz is used by attackers the world over and having control of the data a Mimikatzer will see is a powerful tool to have. One route to looking for Mimikatz usage is injecting false credentials into lsass and watch for their usage in Active Directory, but tracking that credential usage will require some work on your domain controllers (or your SIEM). With the RDP service back on version 3 Canaries, we can use cmdkey to point attackers at our Canaries, and not have to worry about Active Directory integration.
Let’s start by setting up a Canary as a Windows Server (called \\02-FINANCE-02).
This will take all of 1 minute (if you’re a slow typer).
Now even with the default settings, this Canary looks legit on the network:
You can enrol Canaries into Active Directory, so enterprising attackers will sniff around for it on the network and inevitably try its file shares..
Which gives you that one alert, when it matters.
We put in significant work to make sure that Canaries don’t expose your network to additional attack-surface by running full-blown Operating Systems, while still looking legit enough for an attacker to have to use it.
Markus’ cmdkey trick gives you another way to point an attacker to your bird.
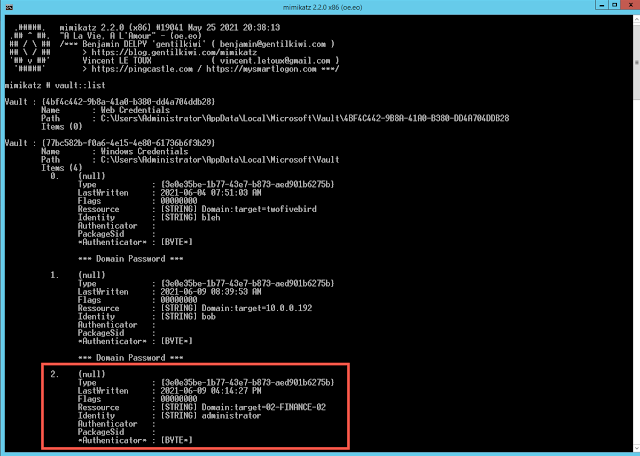
This means that an attacker that compromises this desktop gets bogus credentials [administrator/super-secret-123] but more importantly, they get a pointer to your Canary [\\02-FINANCE-02]
We’re starting to repeat ourselves here, but this gives you that one alert that lets you know when bad stuff is happening.