Attackers on your network love finding stray credentials. They are an easy way to elevate privileges and are often one of the first things attackers look for during post-exploitation.
There’s no shortage of places where these credentials can be found and surprisingly, there’s very little downside to attackers trying them…
…unless there’s a way to drop decoy credentials. This isn’t a new idea, but it usually requires heavy tooling and configuration.
Our newest AD tokens allow you to create fake credentials that can be left in all the familiar places, but without a heavy software component. A single, light-weight script that runs on your Domain Controller lets you know when the fake credentials are used.
Lets walk through typical usage:
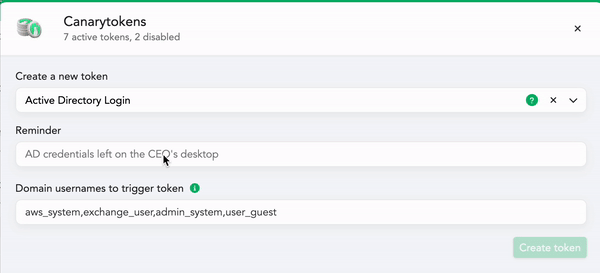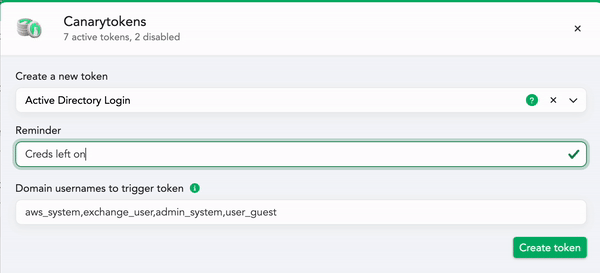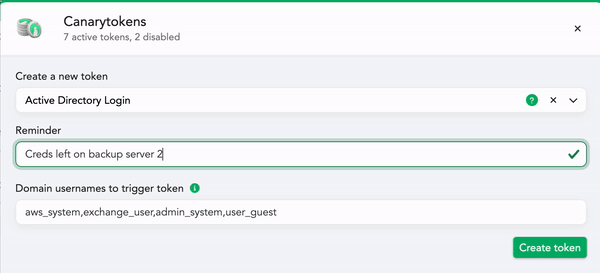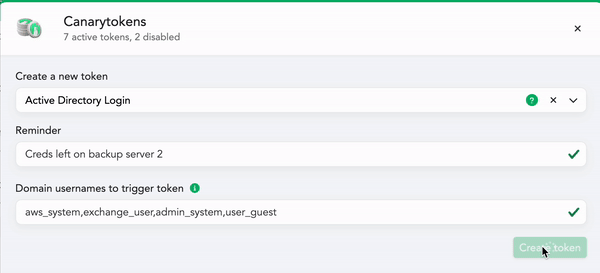
- Head over to your console to create a new “Active Directory Login” token:
- You’ll need to add:
- A Token reminder, which is a note to your future-self reminding you where you placed the fake credentials. It’s possible that this token will fire months from now, when you’ve forgotten where you deployed it. The token reminder could be something like: credentials left in unattend.xml files on the backup server.
- A few fake usernames which when used will trigger the token (we’ll suggest some randomized plausible candidates for you automatically).
- You can download these credentials as an unattend.xml file and/or as a plain text file to leave lying around.
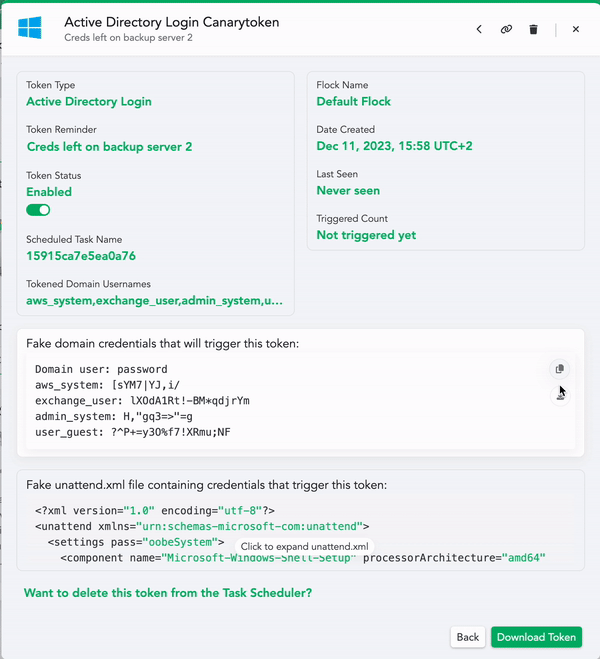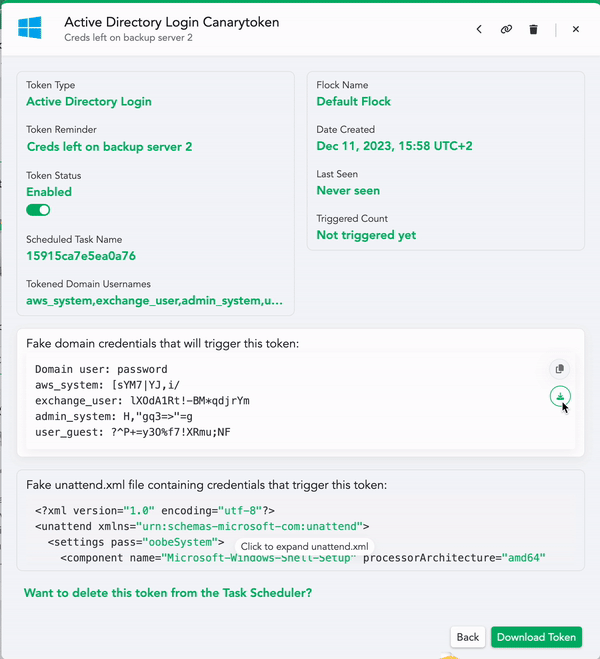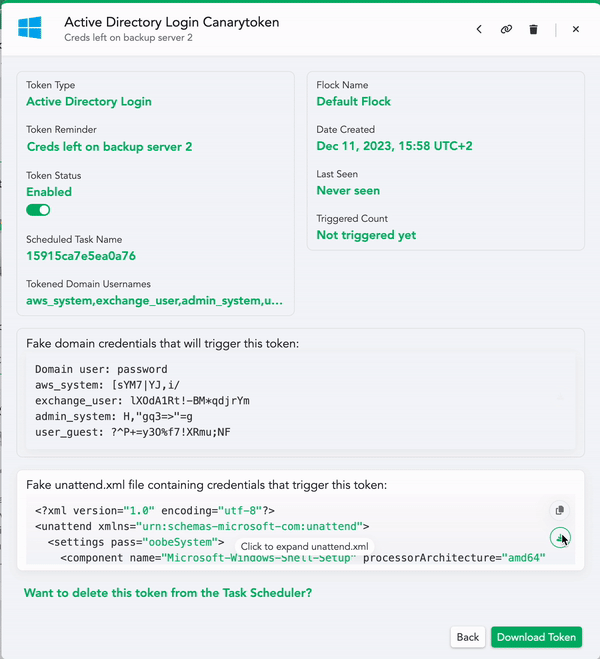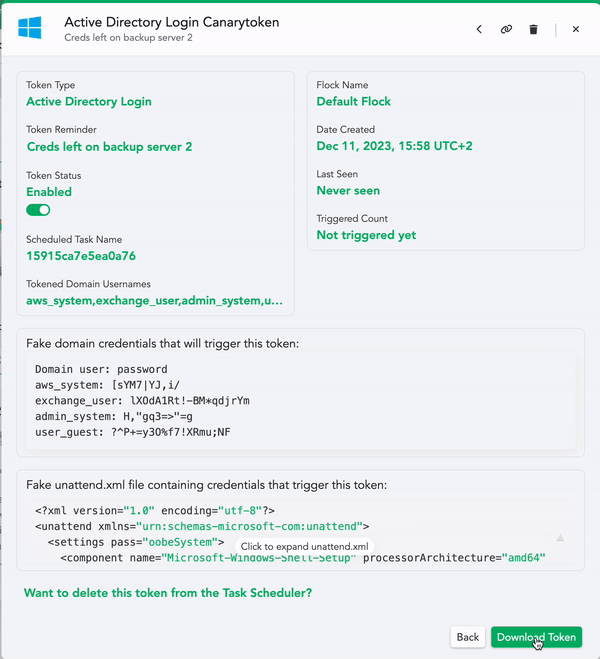
- Then you can download the token itself. This script will create a task on your server that catches the planted credential (attempted) usage. Run this script on a Domain Controller to set up the task.
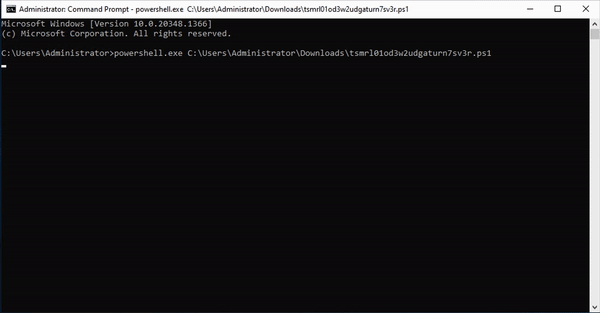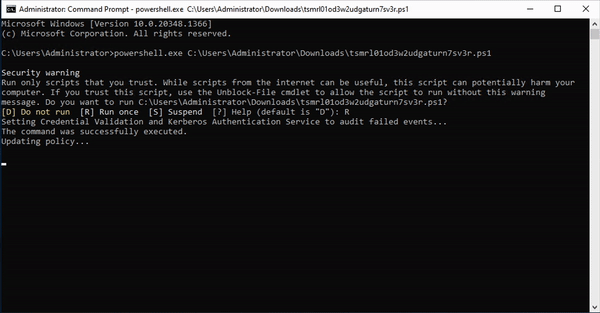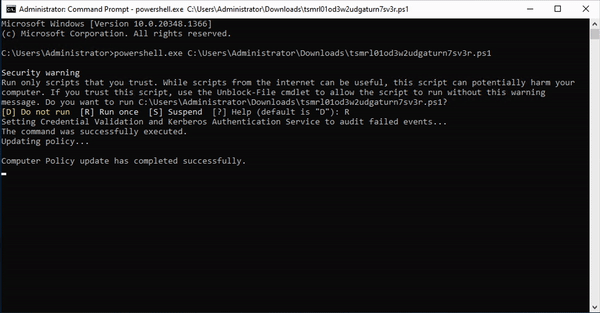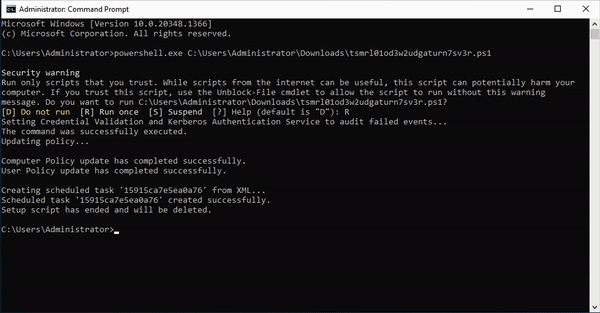
- An attacker who finds these credentials somewhere on your network will try them, which adds entries to event logs. The task processes the event logs and when it sees a login attempt for one of the fake credentials, it will fire off an alert to your Console (and announce their presence).
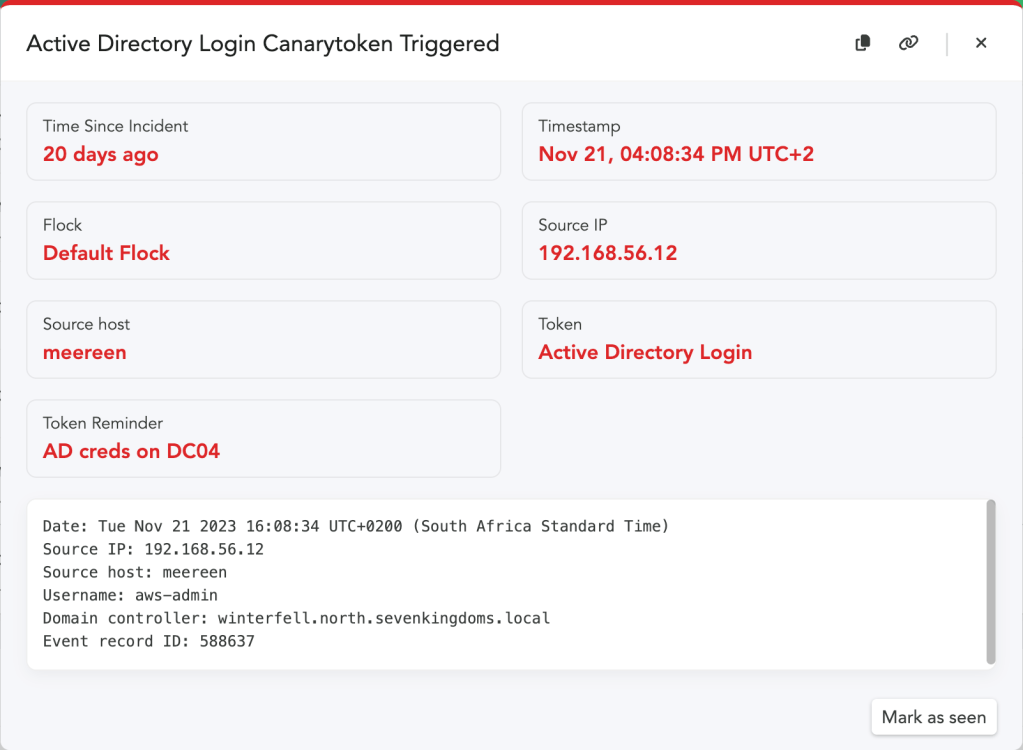
This is an unusual token for us, because it runs a script on your Domain Controller. We’ve kept the script simple and legible so that you can make sure it’s not doing anything nefarious (and so that the script logic can be easily extended). Our work on this token is inspired by IppSec, who showed an initial concept for an AD token that you can catch in his YouTube video here.
If you’d like to take it for a spin, reach out to us here. We’d love to hear how it works out!

1 comments On A (beta) Canarytoken for Active Directory Credentials
Brought this up to our C/S rep in connection with kerberoasting few months back but something like this didn’t exist. Glad it was in the oven and now out as beta : )
Apprised my leaders already.