Introduction The AWS API key Canarytoken is a perennial favourite on Canarytokens.org, and we’ve heard requests for a similar token for Azure. In this blog post, we introduce the Azure Login Certificate Token (aka the Azure Token) to Canarytokens.org1. As with all tokens, you can sprinkle Azure tokens throughout your environment and receive high fidelity notifications whenever they’re used. Place one on your CTO’s laptop, or on every server in your fleet. When attackers breach that laptop, or servers, or …
Category: Uncategorized
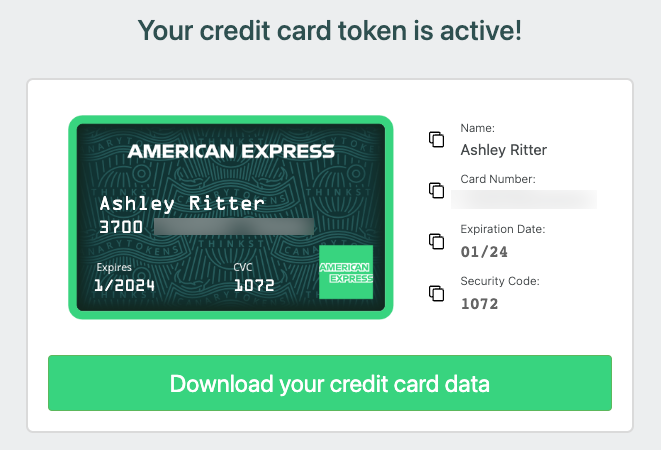
Detect breaches with Canary credit cards! TL;DR; Today we’re releasing a new Canarytoken type: actual credit cards! We recommend placing one anywhere you store payment information. If you ever get an alert on it, you know that that data-store has been compromised. Background Canaries generally aim to look like something an attacker would want to interact with. It’s why our mantra has always been that Canaries should look valuable (instead of just vulnerable). Historically, these have been network services, or …
We’ve written before about the effort we put into UX choices in our app. We don’t consider problems solved just because we kicked out a feature in its general vicinity and we are super strong believers in “small things done well” This came to the fore again recently when we included a “seasonal theme” into customer Consoles and I figured it was worth a brief post to examine our thinking around (even) short-term UX. In our early days we’d give …
I recently discovered “Hot Ones” on YouTube. If you haven’t seen any of the episodes, you should (because they really are fantastic). This isn’t really a controversial opinion: their YouTube channel has 12 million subscribers and almost 2,6 billion views. The show has a few lessons that I think are worth noticing/stealing. I’ll discuss 3 of them here (even if they are kinda random). 1) Genuine Warmth One would expect the show to lean on a kinda gotcha-slapstick routine: we all laugh …
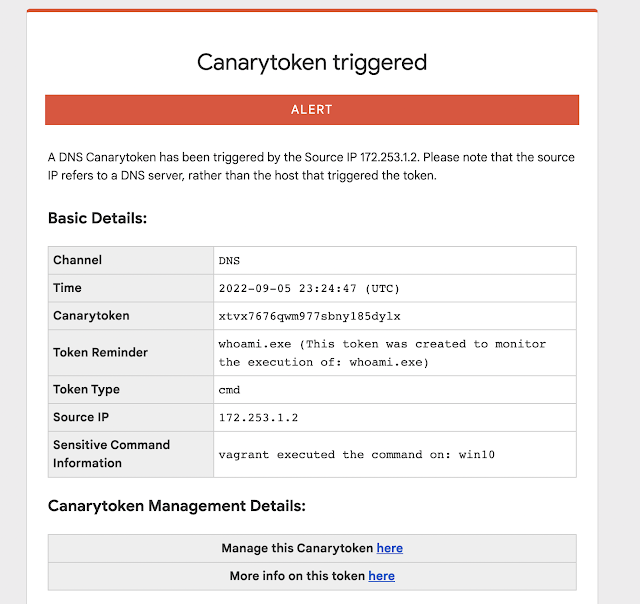
Introduction: Many people have pointed out that there are a handful of commands that are overwhelmingly run by attackers on compromised hosts (and seldom ever by regular users/usage). Reliably alerting when a user on your code-sign server runs whoami.exe can mean the difference between catching a compromise in week-1 (before the attackers dig in) and learning about the attack on CNN. Introducing our new Sensitive Command Canarytoken. This quick/simple Canarytoken alerts you any time your chosen command is executed on …
Introduction This post is the first in a series by Canary customers where they detail how they integrated Canaries and Canarytokens into their security practice. This series hopes to showcase how organizations of varying sizes and structures deployed and acted on alerts to improve the security of their networks. Casey Smith recently joined Thinkst Labs, today he’s sharing his experiences with Canaries and Canarytokens from his previous role as a customer. Background Prior to joining Thinkst, I worked for a …
We discussed this Scott Forstall clip internally and figured it was worth sharing since theres so much going on in just 5 minutes. Bradley commented on how familiar it felt to how we roll and it’s worth digging in to this little more. Quick Background In 2007 Apple was not yet a trillion dollar company, but its star was definitely on the rise. Jobs was back, OSX was taking root and the iPod was game changer. (Their market cap was …
Given the importance of REST API endpoints for most networks and applications, we wanted a way to use (existing) Canarytokens, or Canaries to detect unauthorized access to a REST API. (Like all things Canary) We wanted something easy to use that delivers immediate value. Here we present several new approaches, and look forward to hearing from the community on the usefulness and ways to increase insight here for network defenders. Challenge: APIs are everywhere and permeate most organization’s daily web …
The AWS API Key Canarytoken (paid and free) is a great way to detect attackers who have compromised your infrastructure. The full details are in a previous blogpost, but in short: You go to https://canarytokens.org and generate a set of valid AWS API credentials; Simply leave those in ~/.aws/config on a machine that’s important to you Done! If that machine is ever breached, the sort of attackers who keep you up at night will look for AWS API credentials, and …
To see a World in a Grain of Sand Rice – William Blake mh If you are on TikTok (or a fan of talk shows) at the moment then, no doubt, your feed has included coloured rice being tossed in the air in the form of song lyrics, beloved cartoon characters, and even famous faces. @mr.riceguy Whilst coloured rice is not a new thing (for most preschool teachers, it is a cheap and effective way to keep kids entertained), a bunch of …