Like many in the industry, we are mentally preparing for the trip out to Las Vegas for the US’s crowning trio of big security conferences: BSidesLV, Black Hat USA, and DEF CON. Every year tens of thousands make the annual pilgrimage to the “Hacker Summer Camp” trifecta to see friends, learn from the smorgasbord of tasks and trainings, and share their knowledge far and wide. Each year we at the ThinkstScapes HQ find great content worth highlighting from these longstanding …
Author: Jacob Torrey
Introduction A counterintuitive truth is that great products are defined by both the features they include, as well as those they don’t. We spend a lot of time pondering potential new features for Thinkst Canary to make sure the added value exceeds the inevitable cognitive complexity that new features (or new UX elements) bring. This post will dive into a recent Labs research effort that we ended up leaving on the cutting room floor. Background We are always on the …
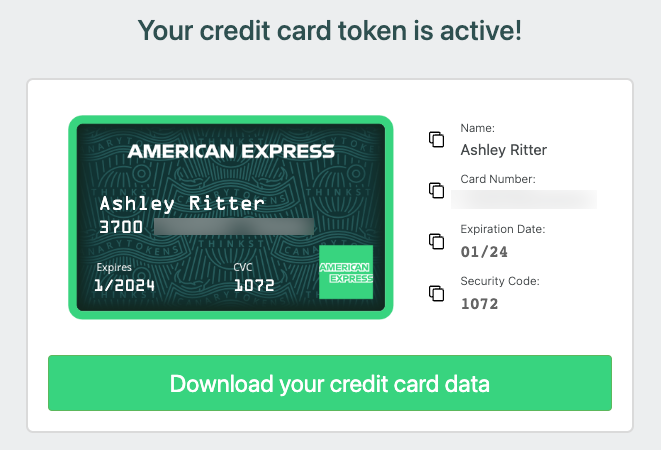
TL;DR Our credit card Canarytokens are out of beta and flying to your consoles! We love these tokens because they provide a novel way to alert on a strong signal of badness. They also perfectly embody our concept of conspicuous deception. Conspicuous deception is our take that simply knowing that a credit card could be a Canarytoken adds risk to the process of stealing, selling, testing, and committing fraud on all cards. Now, fraudsters have to worry that testing or …
Every August, 1000s of people from all over the world consciously decide to brave the balmy 40C/100F+ desert to learn, share, and socialize at the trifecta of Hacker conferences. Whereas Black Hat and DEF CON attendees have been making the sojourn for decades, 2024 marks the 13th year since BSides Las Vegas was added to the mix, lovingly referred to as the “Hacker Summer Camp”. With such a overwhelming buffet of content, we thought it might help to share the …
Front matter In a previous post, Casey talked about our Cloned Website Canarytoken and how it fares against modern phishing attacks. Today, we are releasing two new versions of the token which alert you when an attacker is using an Adversary-in-the-Middle (AitM) attack against one of your sites. An added bonus is that the new tokens can be deployed on properties you only have limited administrative access to (like your Azure tenant login portal or hosted blog). In this post …
Introduction Today we’re open-sourcing a research project from Labs, ZipPy, a very fast LLM text detection tool. Unless you’ve been living under a rock (without cellphone coverage), you’ve heard of how generative AI large language models (LLMs) are the “next big thing”. Hardly a day goes by without seeing a breathless article on how LLMs are either going to remake humanity, or bring upon its demise; this post is neither, while we think there are some neat applications for LLMs, …
Detect breaches with Canary credit cards! TL;DR; Today we’re releasing a new Canarytoken type: actual credit cards! We recommend placing one anywhere you store payment information. If you ever get an alert on it, you know that that data-store has been compromised. Background Canaries generally aim to look like something an attacker would want to interact with. It’s why our mantra has always been that Canaries should look valuable (instead of just vulnerable). Historically, these have been network services, or …
(The making of a MySQL Canarytoken) tl;dr Consider this scenario: An industrious attacker lands on one of your servers and finds a 5MB MySQL dump file (say, called prod_primary.dump). What do they do next? Typically, they would load this dump-file into a temporary database to rummage through the data. As soon as they do, you get an email/SMS/alert letting you know: Eds note: You can create and deploy these by visiting canarytokens.org (completely free; no registration needed) There are obvious benefits …