| This is the first post in an ongoing series that aims to examine documented/public breaches with a special focus on Canary and Canarytoken deployment. The posts do not intend to imply that we would have been a silver bullet and prevented the breach; rather, our approach has been to help detect breaches. These posts are primarily intended to give our customers and users ideas for possible deployment options. |
We love the work done by the team at the DFIR report whenever they publish another in their long series of case studies. The reports they put out are richly detailed and always provide a great view into real-world attacks. They allow us to reason about real attacks and defenses and, if used correctly, they allow us to learn the lessons we need to without suffering the pain of our own incident. This post focuses on the most recent DFIR Report, IcedID to Dagon Locker Ransomware in 29 Days.
In our blog posts, we will share thoughts on how your organization can use Canaries and Canarytokens to prepare for such attacks before they occur.
It is important when reading a report like this is to ask yourself two questions:
- What if this happened to us?
- Can we (better) prepare for it?
We’ll focus on three techniques of this type of attack and will explain how optimal Canary placement can help you and your organization. Canaries can be deployed in just a few minutes and ”just work”… We know this because we see it happen every week.
There are an almost infinite number of ways to infiltrate an organization, including phishing, supply chain attacks, edge device exploitation, and many more. What we believe is crucial, are the actions an attacker takes once they gain initial access.
The industry often over-indexes on the former (which is a constantly moving target) while ignoring the latter which is relatively consistent by its very nature.
Attacker Technique #1: Discovery using common , built in tools
In this breach, the attacker gained access via phishing and set up persistence via scheduled tasks. They then started running common enumeration commands.

Zooming into the details, we can see the common commands that were executed in sequence on the initially compromised hosts.

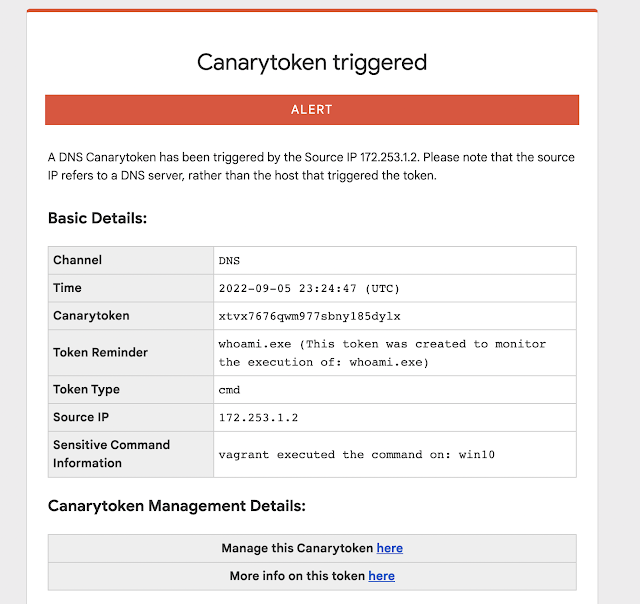
Canary Defense #1: Deploy Sensitive Command Tokens to help alert you when rare or suspicious commands are executed on an endpoint.
Proactive monitoring for suspicious commands is highly beneficial for early detection. We have a lightweight Sensitive Command Token that allows you to easily monitor for the execution of any Windows process and receive alerts whenever that command is executed.
You can configure sensitive command alerts for common system administrator tools used by attackers during reconnaissance or lateral movement stages. By keeping an eye on the execution of such tools, you can quickly identify and respond to potential intrusions or malicious activity within your environment.
Examples from this DFIR post include: nltest.exe, adfind.exe, systeminfo.exe, sharphound.exe
Attacker Technique #2: Locating clear text credentials in files
Reading further in the report we see that the threat actor located and reviewed documents containing passwords for the organization.
A recurring security risk that plagues many organizations is the storage of plaintext credentials within files. Attackers actively search for and then exploit these credentials to expand their access on a network.

Canary Defense #2: Clear text passwords discovered and used.
Interestingly, whenever you discuss Canaries or Canarytokens with a relative newcomer, their first reaction is: “But would an attacker really open a file called passwords.xls?”. Their disbelief is reasonable, except if you’ve done any sort of red-teaming or incident response over the years. Experience tells us real networks do include such files, and attackers know this.
Credential files are attackers’ meat and potatoes so we have a bunch of different ways to trip up attackers.
The first one is dead simple. Create a Canarytokene’d Office document and drop it on a share/server.

Will an attacker resist opening network-passwords.xls ? They can’t resist it because expanding their reach is their current mission, and when they do, you get that one alert that lets you know that badness is happening.

The next one to try is our Active Directory Login Token. It allows you to create fake accounts in your environment. If an attacker then tries using those credentials by authenticating in the AD with these credentials, you receive an alert. (We also give you some files that can be strewn around with those bogus creds).


Fake credential files are easy to deploy and actually give you a strong signal if deployed correctly. Canarytokens make them dead simple to manage.
Attacker Technique #3: Enumerate and access network shares
On the second day of the intrusion, the attackers started to look for accessible network shares.

The DFIR Report has an excellent detailed write up on how attackers enumerate shares.
Canary Defense #3: File share enumeration and access
With Canary you can easily deploy a file share and within minutes you’ll have a juicy target that attackers can’t resist. In fact, upon initial setup our Canary already has a default share waiting to be discovered.
You can also add your own custom files as well.

Further, when deploying a file share Canary, you can leverage the Industry Specific File Share option to automatically generate directory structures and files that match your industry.
When attackers scan for shares and begin to open or copy files. You get an alert.
In order to increase the likelihood of being discovered. You can join your Canary to an Active Directory Domain to make it both discoverable as well as advertise various services an attacker might be interested in. Such as, SMB (File Shares) or RDP (Remote Desktop).
Joining your Canary to Active Directory is simple, and only takes a few minutes.

Once joined, your Canary shows up in both enumeration of Active Directory computers as well as network shares.
Conclusion:
While every intrusion is unique, some patterns repeat. Deploying Canaries and Canarytokens take literal minutes but greatly tip the odds in your favor. Know. When it Matters!