This is the first post in an ongoing series that aims to examine documented/public breaches with a special focus on Canary and Canarytoken deployment. The posts do not intend to imply that we would have been a silver bullet and prevented the breach; rather, our approach has been to help detect breaches. These posts are primarily intended to give our customers and users ideas for possible deployment options. We love the work done by the team at the DFIR report …
Author: Casey Smith
Our Cloned Website Token has been available for a long time now, both on our public Canarytokens.org site as well as for our Canary customers. It’s helped users all over the world detect attacks early in the process. We wanted to take a moment and go over some of the details of this token: how it works, how to create and use one, and critically, how it fares against the new “Adversary-in-the-Middle” (AitM)-generation of phishing attacks.. The cloned website token …
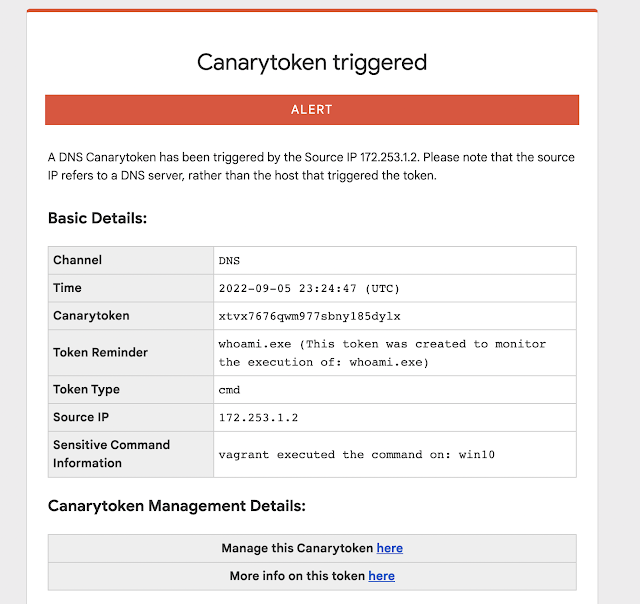
Introduction: Many people have pointed out that there are a handful of commands that are overwhelmingly run by attackers on compromised hosts (and seldom ever by regular users/usage). Reliably alerting when a user on your code-sign server runs whoami.exe/klist.exe/nltest.exe/etc. can mean the difference between catching a compromise in week-1 (before the attackers dig in) and learning about the attack on CNN. Introducing our new Sensitive Command Canarytoken. This quick/simple Canarytoken alerts you any time your chosen command is executed on …
Introduction This post is the first in a series by Canary customers where they detail how they integrated Canaries and Canarytokens into their security practice. This series hopes to showcase how organizations of varying sizes and structures deployed and acted on alerts to improve the security of their networks. Casey Smith recently joined Thinkst Labs, today he’s sharing his experiences with Canaries and Canarytokens from his previous role as a customer. Background Prior to joining Thinkst, I worked for a …
Given the importance of REST API endpoints for most networks and applications, we wanted a way to use (existing) Canarytokens, or Canaries to detect unauthorized access to a REST API. (Like all things Canary) We wanted something easy to use that delivers immediate value. Here we present several new approaches, and look forward to hearing from the community on the usefulness and ways to increase insight here for network defenders. Challenge: APIs are everywhere and permeate most organization’s daily web …